APPLICATION
SECURITY
CAREER PATH
Become an Application Security Specialist
"*" indicates required fields
CERTIFIED PROFESSIONALS
IN 145 COUNTRIES






"*" indicates required fields













"*" indicates required fields

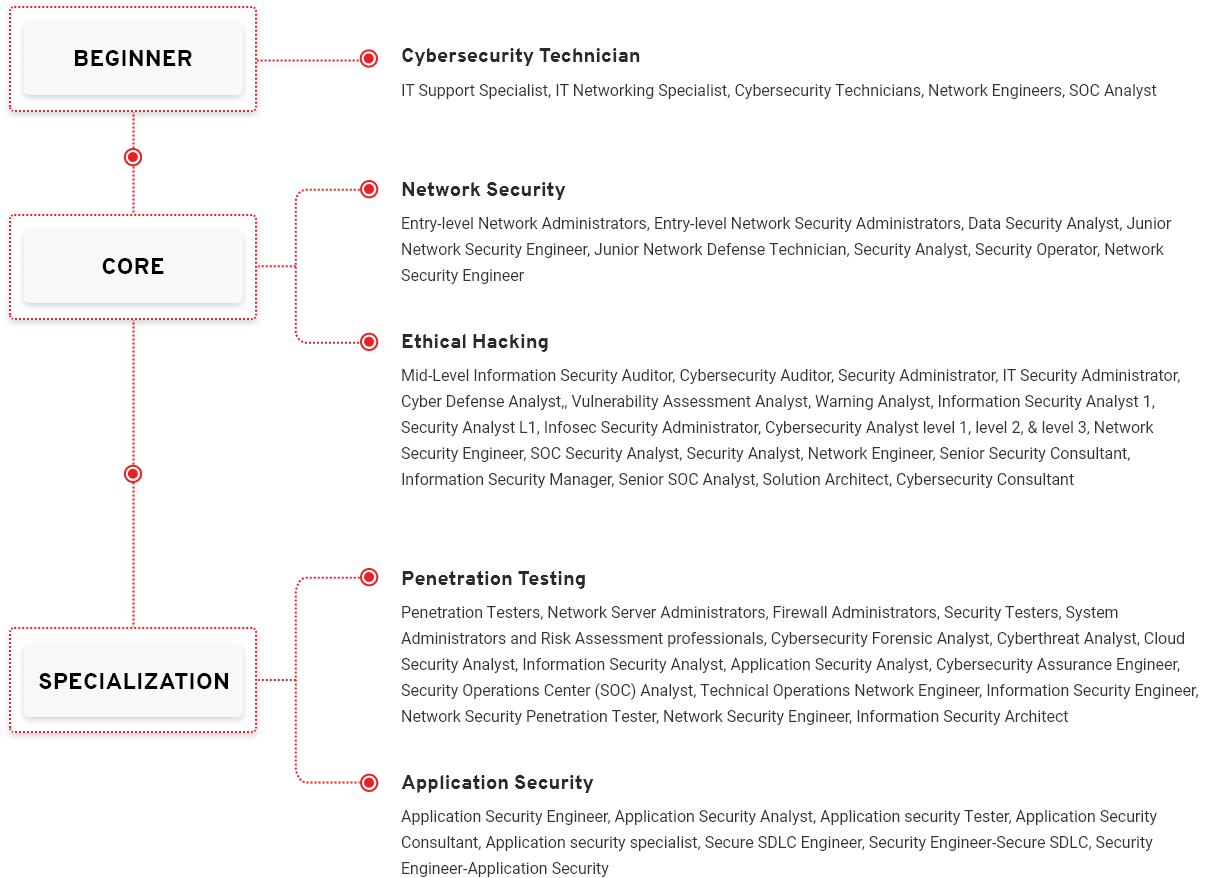
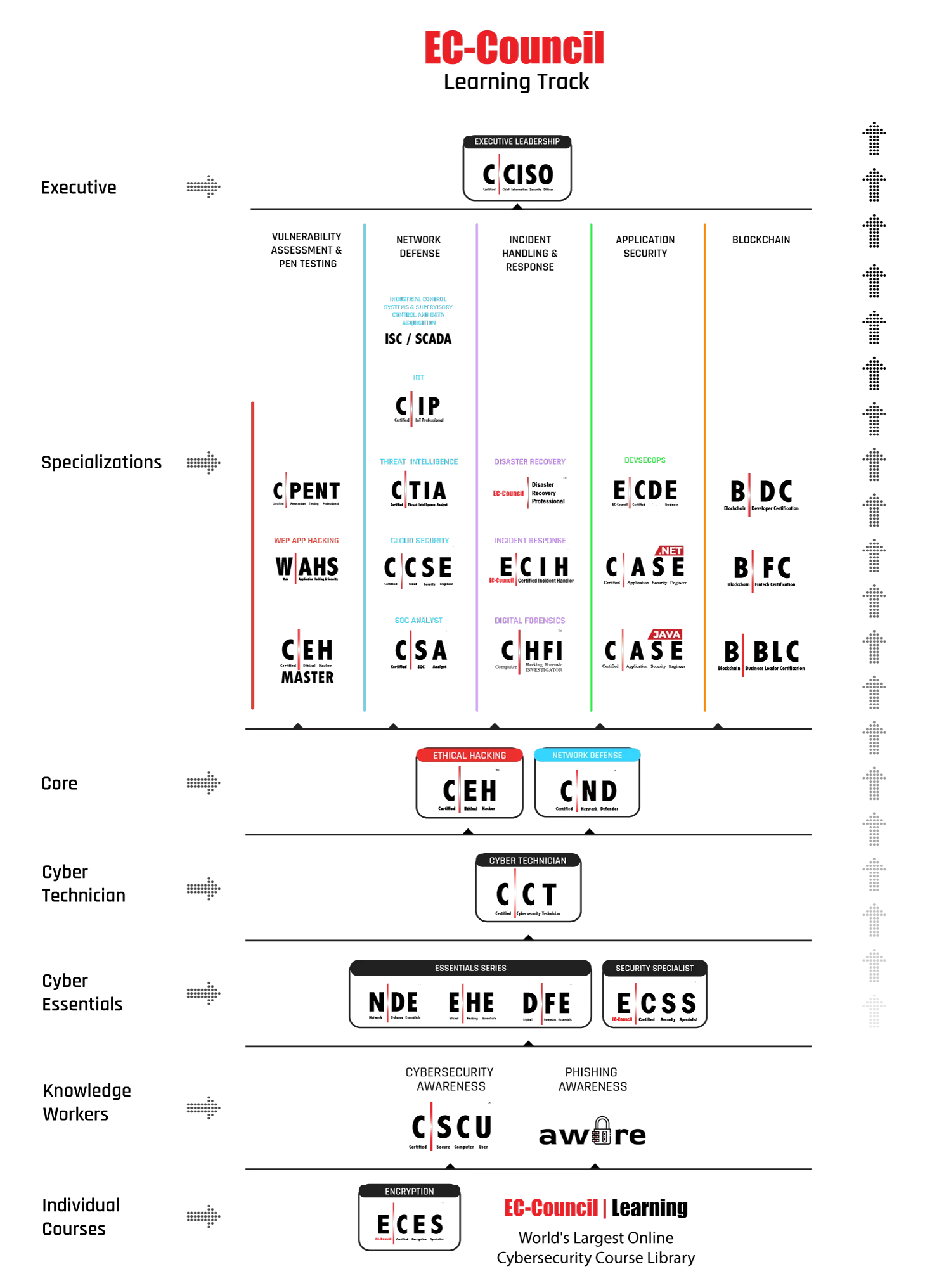
A novice should begin their journey by building a solid foundation in the core areas of cybersecurity. Start by getting the basics right with the Network Defense, Ethical Hacking, and Digital Forensics certification; the course to prepare for this certification is completely free.
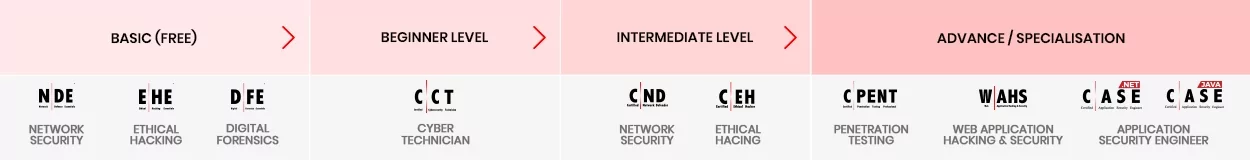
Attain a basic core certification of the Certified Cybersecurity Technician (C|CT) to begin your professional cybersecurity course. C|CT will immerse students into well-constructed knowledge transfer through training, accompanied by critical thinking challenges and immersive, hands-on lab experiences allowing candidates to apply their knowledge and move into the phase of skill development right in the class.
Post C|CT, you need to grow your career path with the Certified Network Defender certification. You will learn to examine network traffic at the binary level, master TCP/IP protocol, introduce vulnerability assessments and hacking methodology, and much more. These are essential skills that a VAPT professional should possess, a good foundation to become a network security expert.
Once you have a solid foundation, you will be ready to move into ethical hacking with Certified Ethical Hacker (C|EH) course, Worlds No.1 Ethical hacking certification. C|EH learning framework Learn, Certify, Engage and Compete framework covers a comprehensive training program to prepare you for the certification exam and the industry’s most robust, in-depth, hands-on lab experience of any cybersecurity program available. The C|EH certification will help you get into the Hackers mindset and expose you to the 5 phases of ethical hacking, which will allow you to acquire the skills to become a competent professional in the application security world.
Post C|EH, we recommend you take up Web Application Hacking and Security, a specialization certification that enables you to play, learn, hack, test, and secure web applications from existing and emerging security threats in the industry verticals.
After mastering the 5 Phases of Ethical Hacking, you will be ready for penetrating testing. With the Certified Penetration testing Professional course will learn advanced penetration testing skills such as Advanced Windows Attacks, Internet of Things (IoT) Penetration Testing, Penetration Testing in OT and ICS/SCADA Environments, Exploit Writing and Advanced Binary Exploitation, Bypassing Filtered Networks, Accessing Hidden Networks with Pivoting and Double Pivoting, Privilege Escalation, Defense Evasion, Attack Automation with Scripts and many more.
In this capstone course of C|ASE.Java and C|ASE.Net you will learn about the 5 phases of secure SDLC methodologies, and planning, creating, testing, and deploying an application.

"*" indicates required fields